- Nonmalicious and malicious program flaws
- Viruses
- An error is a mistake in the software.
- An error may lead to an incorrect state, or fault (one error may lead to many faults)
- A fault may cause the system to depart from its required behavior. Such departure is a failure.
- "Penetrate and patch"
- May result in worse security
- Almost impossible to assure that a program does what is intended and nothing more
- Software engineers are not "security conscious"
- validation error
- domain error
- serialization and aliasing
- inadequate authentication/authorization
- boundary condition violation
- other exploitable logic errors
- Buffer overflows --- like trying to pour 2 quarts of water
into a 1 quart pitcher
char array[10]; for(i = 0; i < 10; ++i) array[i] = `A`; array[10] = `B`;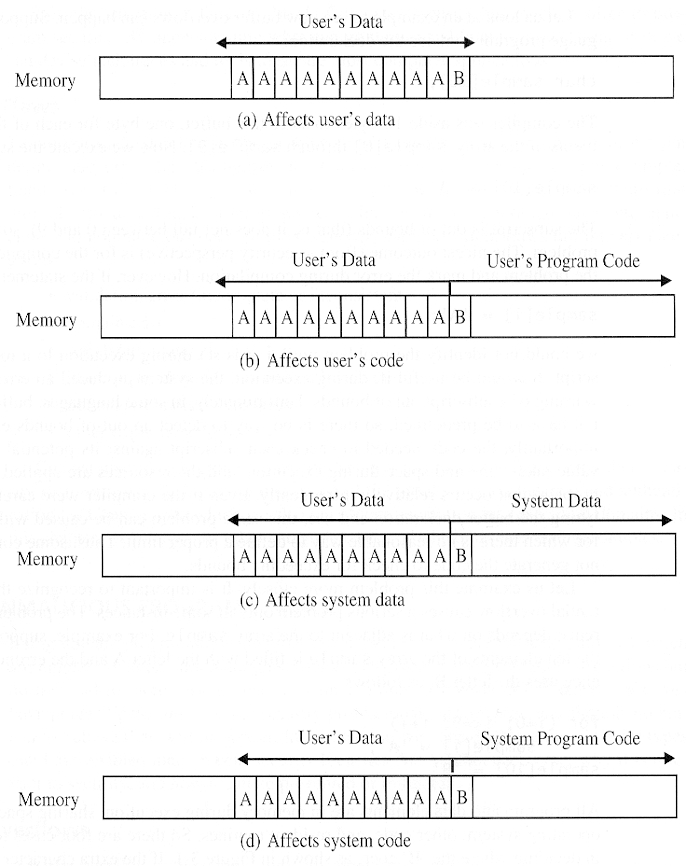
- "Smashing the stack" --- redirect execution to attacker's code (attack
of the decade)
- Incomplete mediation
- Example: data checked when input
on client, but not checked after returned to server
http://www.things.com/orders/final&custID=112&num=555A &qty=20&price=10&shipping=5&total=205changed (by client) tohttp://www.things.com/orders/final&custID=112&num=555A &qty=20&price=10&shipping=5&total=25 - Example: Linux kernel
- Example: data checked when input
on client, but not checked after returned to server
- Combinations of program flaws
- Malicious code can do much harm
- Malicious code has been around for a long time (early 80's or before)
- Work of Fred Cohen
- Types of malicious code
- virus --- attaches itself to a program and copies itself to other programs
- trojan horse --- program with unexpected additional functionality
- logic bomb --- triggers action based on some event
- trapdoor --- allows unauthorized access
- worm --- propagates copies of itself through a network
- rabbit --- replicates itself without limit (exhausts resources)
- How viruses attach
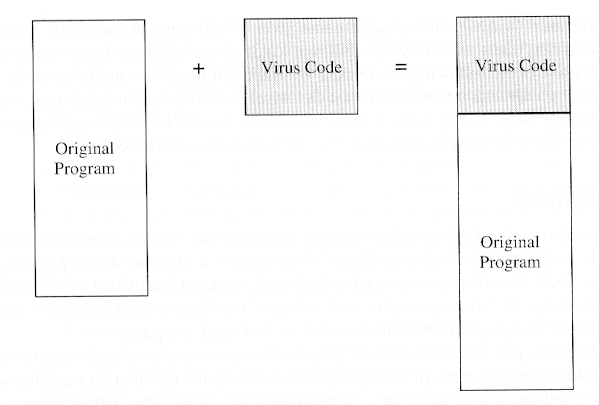
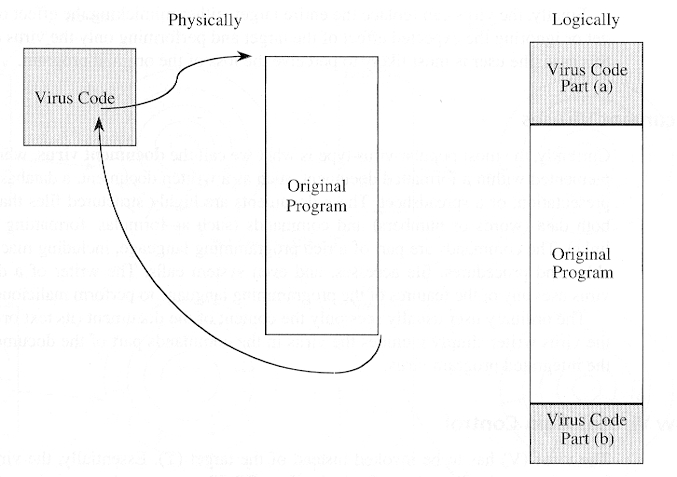
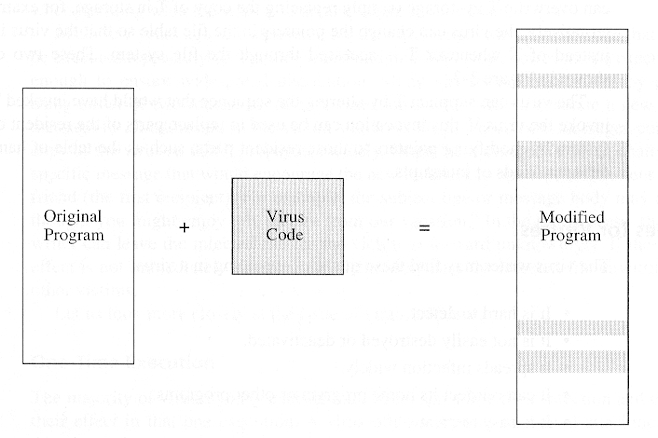
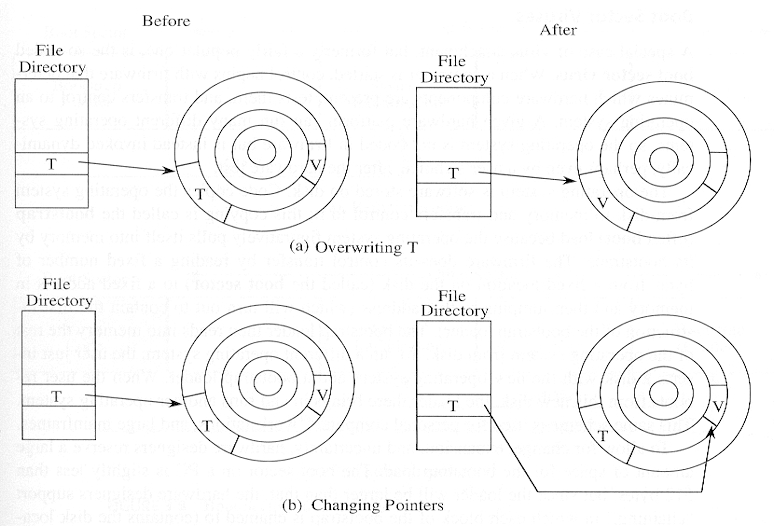
- Virus replacing a program
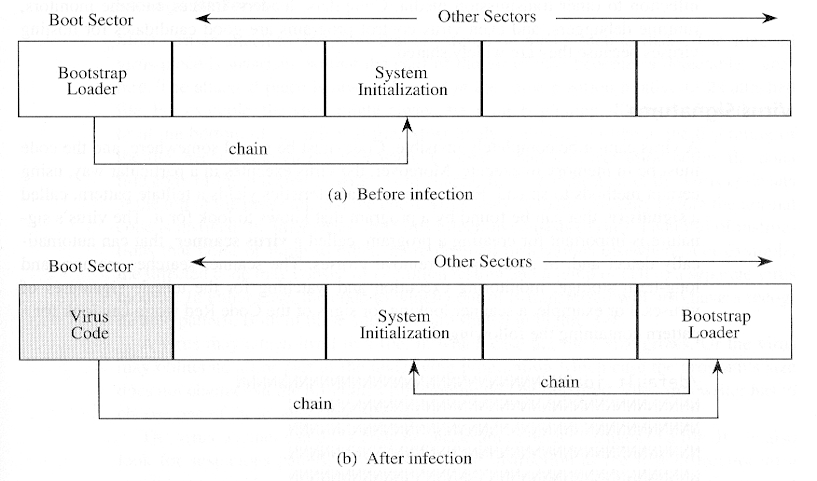
- Boot sector virus
- Other places viruses live
- Memory resident
- Applications (macros, data, etc.)
- Libraries
- Compiler, debugger, virus checking programs, etc.
- Virus signatures
- Polymorphic and metamorphic viruses
- Examples of malicious code
- Brain virus (1986)
- What it does --- places itself in boot sector (and 6 other sectors, one of which contains original boot sector) and screens disk read calls, so that it is not detected
- How it spreads --- with each read, it reads boot sector to see if it is yet infected; if not it infects as above
- What was learned --- a prototype for many later viruses
- Morris worm (1988)
- What it does --- the worm was designed to
- determine where it could spread
- spread its infection
- remain undiscovered
- Its effect --- "flaw" in code so it tried to re-infect systems, which led to resource exhaustion; also many systems disconnected from network to avoid infection
- How it worked --- exploited known Unix flaws
- Where to spread --- 3 methods:
- user account password guessing (dictionary attack)
- exploit a bug in fingerd (buffer overflow)
- exploit trapdoor in sendmail (debug mode)
- Spread infection --- bootstrap loader (99 lines of C) sent to victim machine and compiled and executed; it then fetched the rest of the worm (victim even authenticated the sending host!)
- Remain undiscovered --- if transmission interrupted, code deleted; full code encrypted and downloaded code deleted; periodically changed its name and process identifier
- Where to spread --- 3 methods:
- What was learned --- sent shock waves through the Internet (of 1988); could have been much worse; led to Computer Emergency Response Team (CERT)
- What it does --- the worm was designed to
- Code Red (2001), Infected more than 250,000 systems in 9 hours;
overall more than 750,000 servers affected (6,000,000 susceptible
servers at the time)
- What it did --- exploited buffer overflow in Microsoft Internet Information Server (IIS) software; then checks traffic on port 80 to infect other systems
- What effect it had --- first version
HELLO! Welcome to http://www.worm.com ! Hacked by Chinese!Original version: From day 1 to 19 of a month it tried to spread; from 20 to 27 a DDoS attack on www.whitehouse.gov (later version included a Trojan horse allowing attacker remote access) - How it worked --- later version created a trapdoor via trojan; rebooted system to flush worm (but leaving back door and trojan)
- What was learned --- might be a "beta test for information warfare"
- Flash worm (future), Slow worm, etc.
- Brain virus (1986)