- Challenge/response (login only)
- Mutual authentication
- Integrity/encryption of data
- Mediated authentication
- Nonce types
- Picking random numbers
- Performance considerations
- Authentication protocol checklist
- A bad idea
- Alice sends name and password in clear (across network) to Bob
- Bob verifies name and password and communication proceeds
- Better idea using shared secret
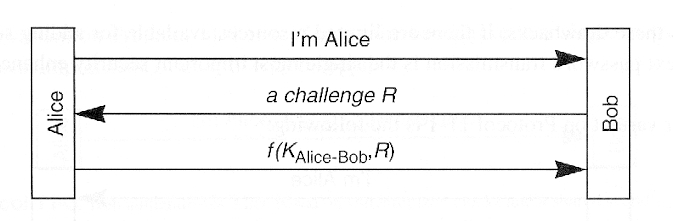
- Implications
- Authentication is not mutual
- How to encrypt subsequent conversation?
- If key derived from a password, offline password guessing is possible
- Bob knows KAlice-Bob so if Bob's database is compromised, attacker can impersonate Alice
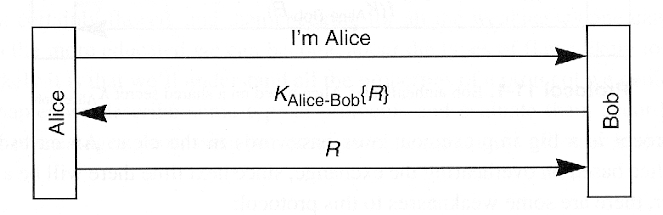
- Implications
- Requires reversible cryptography (hash will not work)
- If R is known and key derived from password, dictionary attack is possible by simply claiming to be Alice
- If R has a limited lifetime, Alice can authenticate Bob (mutual authentication)
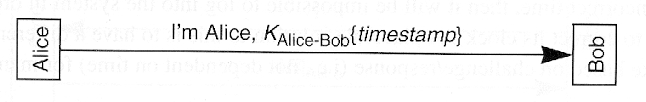
- Implications
- Easy to modify "bad idea" to this form, since no additional messages
- More efficient
- Bob does not need to maintain state
- Eavesdropper can impersonate Alice (within acceptable clock skew); might also be possible to impersonate Alice to another server
- If Bob sets his clock back, intercepted authentication messages can be replayed
- Setting time (and agreeing on time) is a security issue
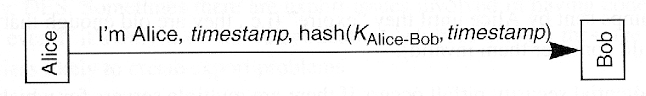
- Implications
- Same as above, but using a hash
- Why transmit timestamp in the clear?
- Implications
- Better idea using public key crypto
(Notation: [R]Alice means sign with private key and {R}Alice means encrypt with public key.)
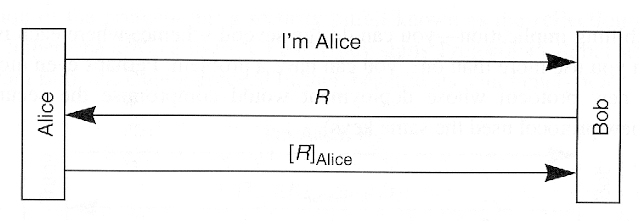
- Implications
- Compromise of Bob's database will not allow attacker to impersonate Alice
- Attacker may be able to trick Alice into signing anything
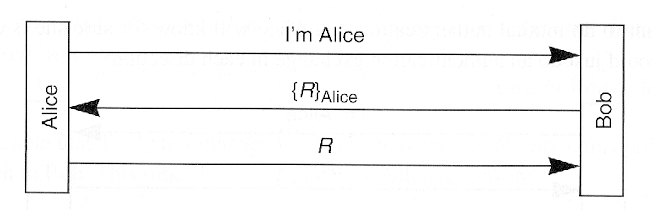
- Implications
- Compromise of Bob's database will not allow attacker to impersonate Alice
- Attacker may be able to trick Alice into decrypting anything
- Implications
- Reflection attack
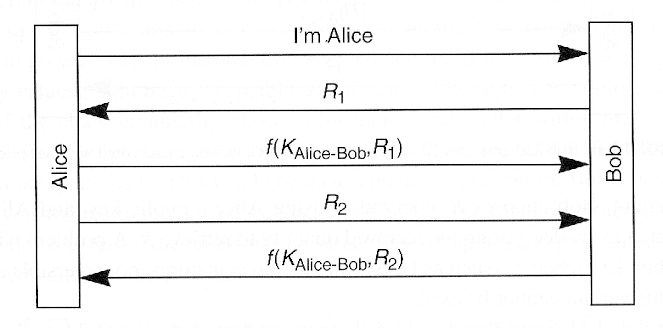
- Implications
- Authenticated exchange in each direction
- Inefficient?
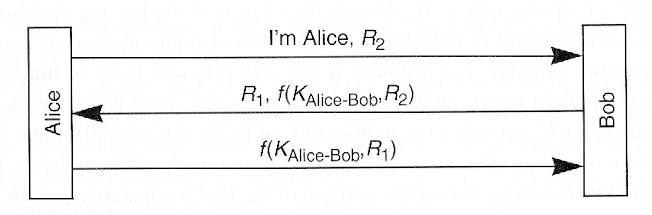
- Implications
- More efficient
- Easy to get chosen plaintext
- Subject to a reflection attack
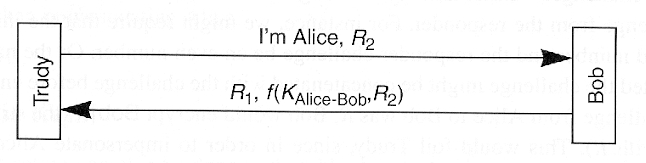
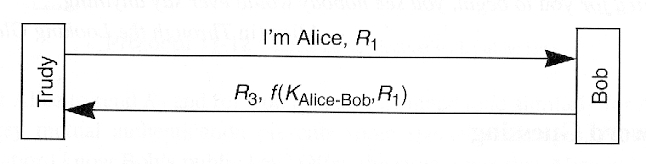
- Attack
- Trudy opens 1st session to Bob
- Trudy opens 2nd session to Bob in order to get information needed to complete 1st session
- Solution?
- Alice and Bob should not do exactly the same thing
- Have Bob encrypt with KAlice-Bob and Alice encrypt with KAlice-Bob+1 or
- Initiator sends odd R, responder sends even R, etc.
- Implications
- Password guessing (chosen plaintext)
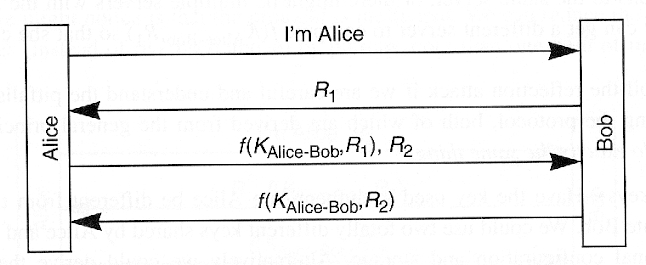
- Implications
- One "extra" message and Alice cannot obtain chosen plaintext
- Implications
- Public keys
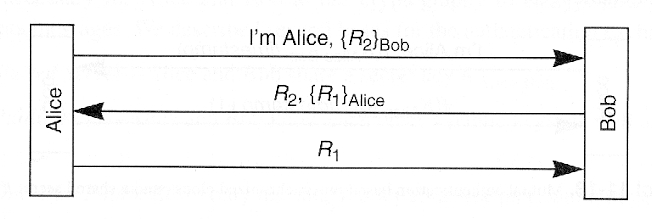
- Implications
- How to obtain public keys?
- How can workstation obtain private key from password? (Easy with symmetric key crypto, not so easy with public key crypto.)
- Identity-based encryption is an active research area
- Implications
- Timestamps
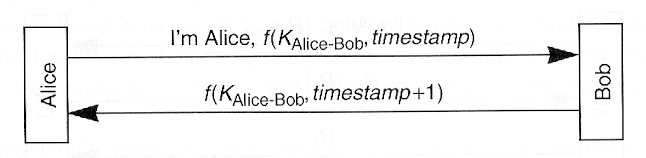
- Implications
- Only 2 messages
- Alice and Bob must encrypt different things
- Everyone must agree on the time
- Time is now security-critical
- Implications
- Shared secret
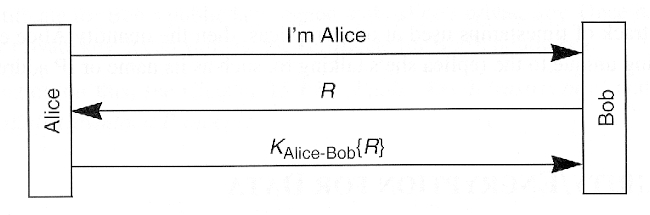
- Implications
- Why not use KAlice-Bob as session key?
- Why not use KAlice-Bob+1 as session key?
- Why not use KAlice-Bob+1 to encrypt R to obtain session key?
- Why not use KAlice-Bob to encrypt R+1 to obtain session key?
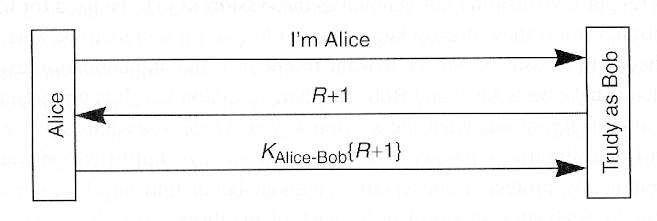
- Implications
- Two-way public key authentication
- Alice sends {K}Bob to Bob
Issues: Trudy can hijack the conversation
- Alice sends [{K}Bob]Alice to Bob
Issues: If Trudy records conversation and later overruns Bob, she can recover K
- Alice sends {K1}Bob and
Bob sends {K2}Alice to Bob.
The session key is K1 ⊕ K2
Issues: Trudy can cause confusion, but cannot recover K
- Alice and Bob do a Diffie-Hellman key exchange, and
sign the quantities: Alice sends
[ga mod p]Alice to Bob and
Bob sends [gb mod p]Bob to Alice
Issues: Even if Trudy overruns both Alice and Bob, she cannot recover K
- Alice sends {K}Bob to Bob
- One-way public key authentication --- similar to
two-way public key authentication
- Privacy and integrity --- key rollover
- In priciple
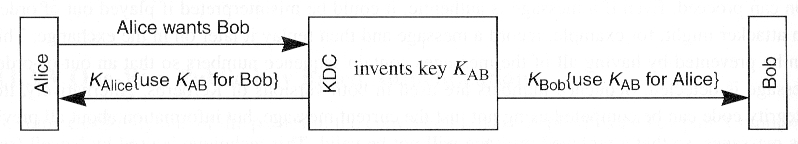
- Implications
- KDC does not authenticate Alice but only Alice can decrypt KAB sent to "Alice"
- Message from Alice to Bob could arrive before Bob gets his key
- Implications
- In practice
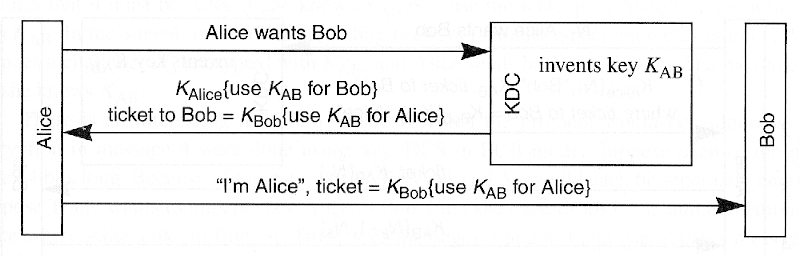
- Implications
- Alice and Bob must still mutually authenticate
- Implications
- Kerberos
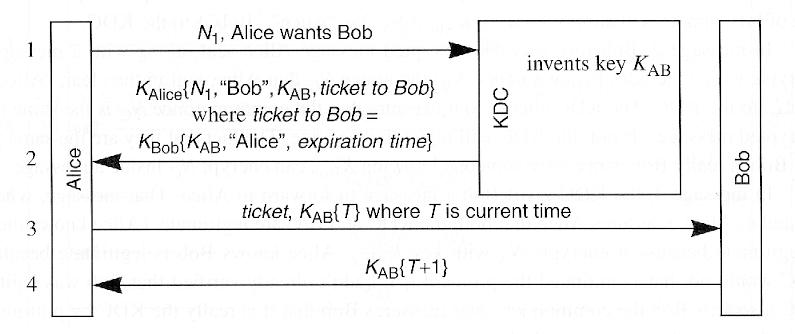
- Implications
- Everyone must agree on time
- Implications
- Unpredictable nonce required
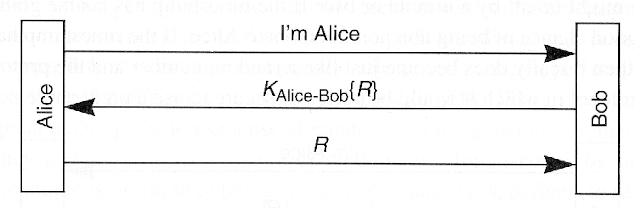
- Predictable nonce is OK
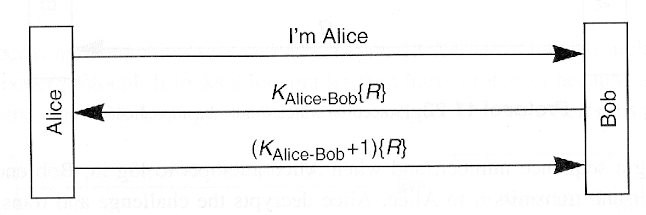
- Different application require different types of "random" numbers
- For pseudo-random number generator, seed value is critical
- Interesting mistakes listed in book
- Number of crypto operations (private key, public key, symmetric key, hash)
- Number of messages transmitted
- Cache previous state? (more speed, less security)
- Eavesdrop
- data?
- replay?
- off-line password (or other secret) guessing?
- Pretend to be Alice
- convince Bob?
- off-line password guessing?
- replay (e.g., impersonate Alice, impersonate Bob)?
- get Bob to decrypt or sign something?
- Pretend to be Bob (accept connection from Alice)
- convince Alice?
- off-line password guessing?
- replay?
- get Alice to decrypt or sign something?
- Read Alice's database (can impersonate Alice)
- impersonate Bob to Alice?
- decrypt old conversations?
- Read Bob's database (can impersonate Bob)
- impersonate Alice?
- decrypt old conversations?
- Examine and/or modify data sent between Alice and Bob
- off-line password guessing?
- read data?
- hijack conversation?
- modify messages without detection?
- Any combination of the above
- For example, even after overrunning both Alice and Bob's databases, it should not be possible to decrypt recorded conversations