Deliverable 3
Description: Implement secret sharing encryption such that users have parts of the secret but no individual holds can individually find the secret. Explore what happens when a sufficient number of users combine their parts of the secret
Implementation steps:
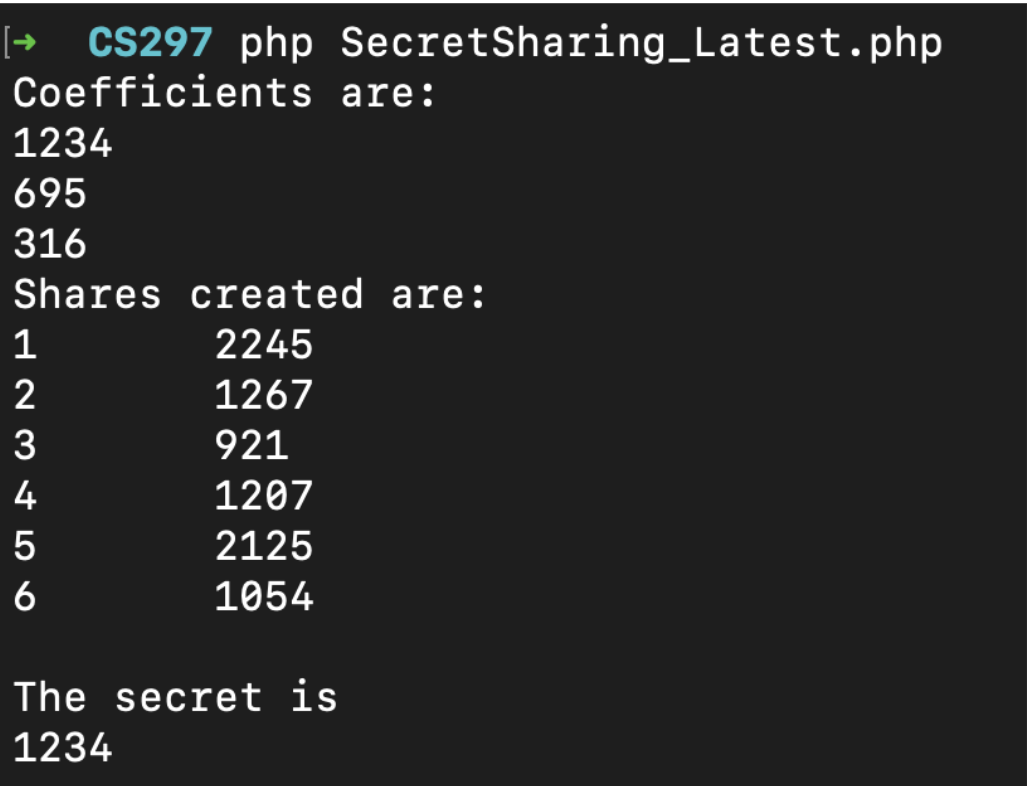
- Decide the number of shares and threshold for secret shares
- Encrypt the secret and generate shares
- To generate shares, create a polynomial with degree = threshold-1
- Evaluate the polynomial and generate x and y coordinates
- To decrypt the secret, get points from threshold number of users
- Use polynomial interpolation to get the secret
Implementation:
Results: