DB2 Concurrency Control
CS185c
Chris Pollett
Apr 27, 2010











CS185c
Chris Pollett
Apr 27, 2010
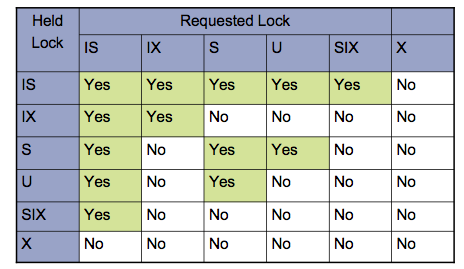
Which of the following statements is true?
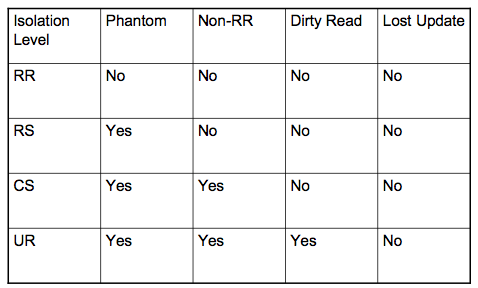
The PREP and BIND commands for application programs have a parameter that controls the isolation level for all transactions executed by the program that is being bound. The parameter consists of the word ISOLATION followed by the abbreviation of the desired level: RR, RS, CS, or UR. The default isolation level, both for application programs and for interactive sessions, is Cursor Stability (CS).
When a table space is created or altered, you can specify the LOCKSIZE option. The choices are:
| held/requested | S | U | X |
|---|---|---|---|
| S | Y | Y | N |
| U | Y | N | N |
| X | N | N | N |