










More DB2 Security
CS185c
Chris Pollett
Apr 22, 2010











CS185c
Chris Pollett
Apr 22, 2010
SET CURRENT SCHEMA = "ABC"; SET CURRENT SQLID = "XYZ"; SELECT * FROM T1;
SELECT 'PRIMARY AUTHID = '||USER, 'CURRENT SQLID = '||CURRENT SQLID, 'CURRENT SCHEMA = '||CURRENT SCHEMA FROM SYSIBM.SYSDUMMY1
Different DB2 object have different available explicit privileges. We next list some of these by object
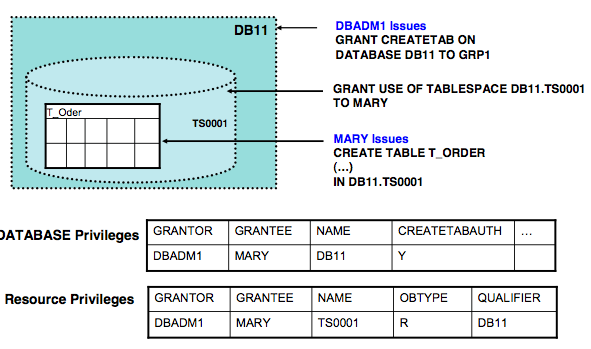
A DB2 GRANT statement gives a specific privilege to an authorization ID. Here are some examples of this command:
GRANT SELECT ON TABLE TABLE1 TO MARY; GRANT BIND ON PACKAGE DBRM1 TO PAYROLL; GRANT SELECT ON TABLE TABLE1 TO ACCNTG; GRANT CREATDB, LOAD ON DATABASE DBMANUF TO MANUF WITH GRANT OPTION;
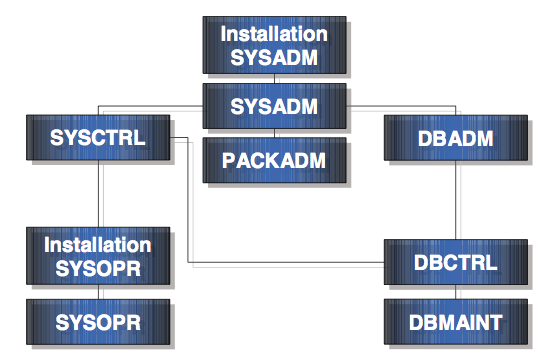
REVOKE privileges ON resource FROM authid (BY authid [SYSADM/SYSCNTL only])
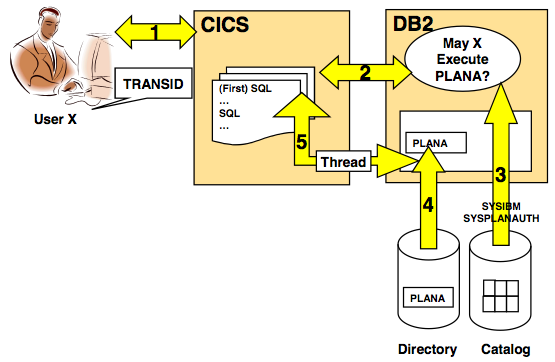
GRANT SYSOPR TO user01; --- Grants user01 the privilege ---to have system operator authority. GRANT DBADM ON DATABASE dbm1 TO user01; --- Grants user01 the database administrator authority.
SECURITY CHAR(8) NOT NULL WITH DEFAULT AS SECURITY LABEL,
CREATE TRUSTED CONTEXT CTX1 BASED UPON CONNECTION USING SYSTEM AUTHID ADMIN1 ATTRIBUTES (ADDRESS '9.67.40.219') ENABLE;
CREATE ROLE CTXROLE; GRANT DBADM ... TO CTXROLE; CREATE TRUSTED CONTEXT CTX1 BASED UPON CONNECTION USING SYSTEM AUTHID ADMIN1 DEFAULT ROLE CTXROLE ATTRIBUTES (ADDRESS '9.67.40.219') ENABLE;
CREATE TRUSTED CONTEXT CTX1 BASED UPON CONNECTION USING SYSTEM AUTHID ADMIN1 ATTRIBUTES (ADDRESS '9.67.40.219') ENABLE WITH USE FOR JOE ROLE JROLE;
An auditable DBA process can be implemented with trusted contexts and roles: