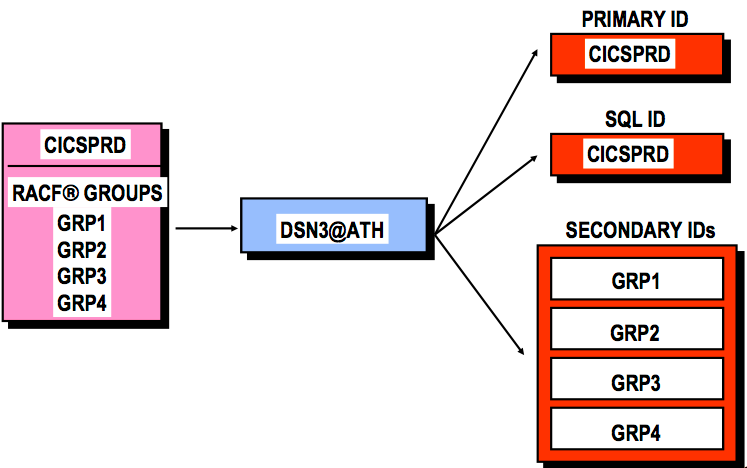
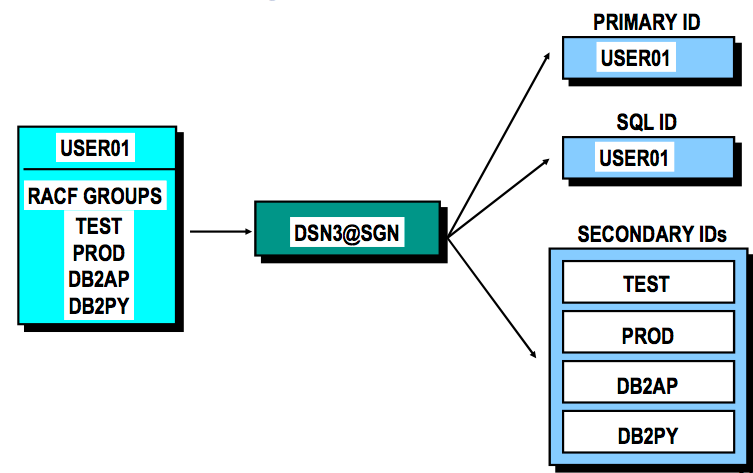
DB2 Security
CS185c
Chris Pollett
Apr 20, 2010











CS185c
Chris Pollett
Apr 20, 2010
Which of the following statements is true?
import java.sql.*;
...
//inside some method
String url = "jdbc:db2:", empNO;
Connection con; Statement stmt; ResultSet rs;
Class.forName("com.ibm.db2.jcc.DB2Driver");
con = DriverManager.getConnection (url);
stmt = con.createStatement();
rs = stmt.executeQuery("SELECT EMPNO FROM EMPLOYEE");
while (rs.next()) {
empNo = rs.getString(1);
System.out.println("Empno=" + empNO);
}
rs.close();
stmt.close();
con.close();
...