Captchas, Firewalls, Protocols
CS166
Chris Pollett
Oct 29, 2012











CS166
Chris Pollett
Oct 29, 2012
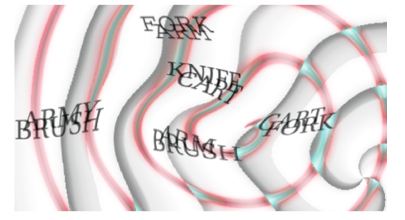
Which of the following is true?
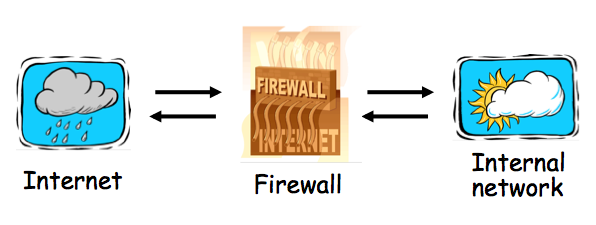

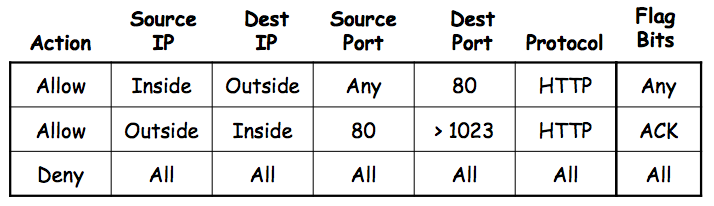
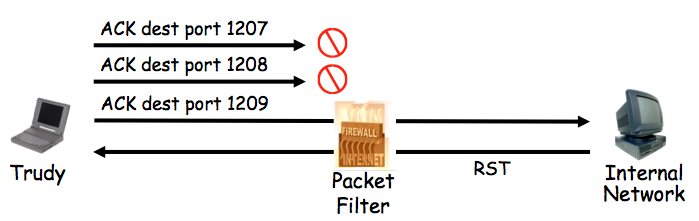

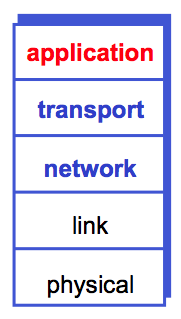
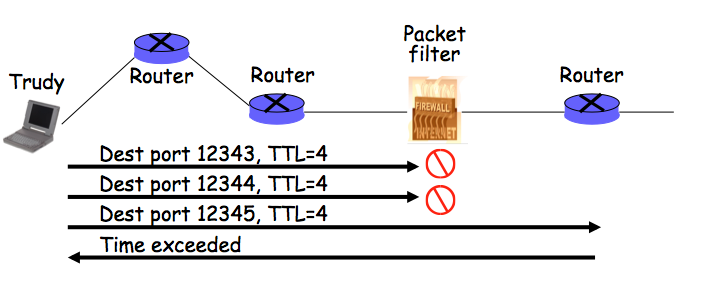
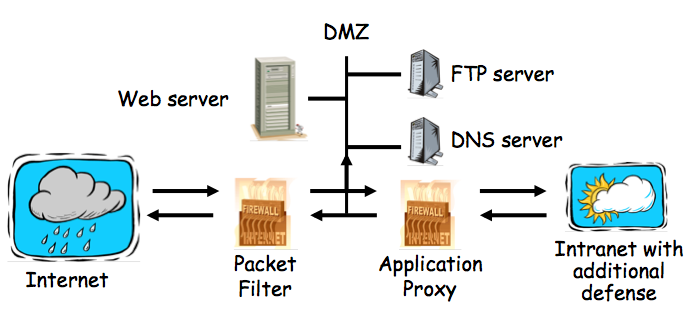
We are now going to start the third major topic of this course -- protocols.
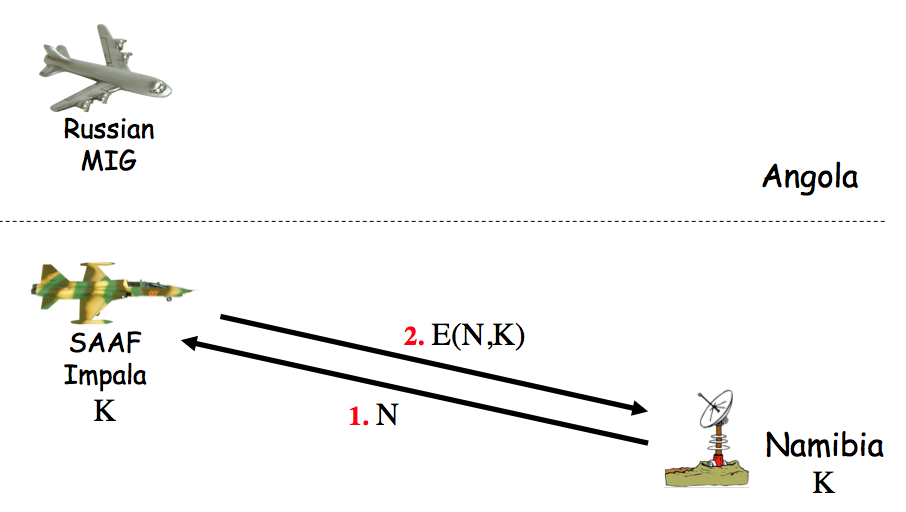
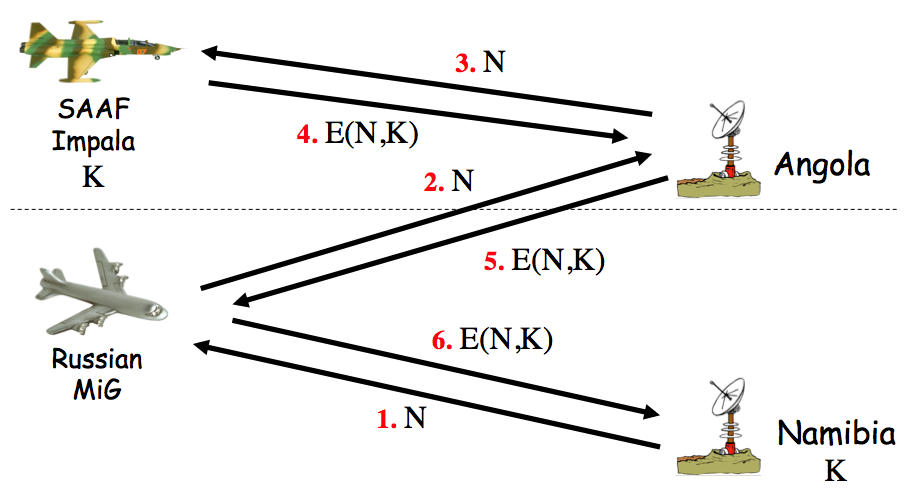
To start talking about protocols we will look at several simple security protocols... First, consider the following protocol for entering the NSA building...