










One-time Pads, Codebook Ciphers, History
CS166
Chris Pollett
Aug. 29, 2012











CS166
Chris Pollett
Aug. 29, 2012
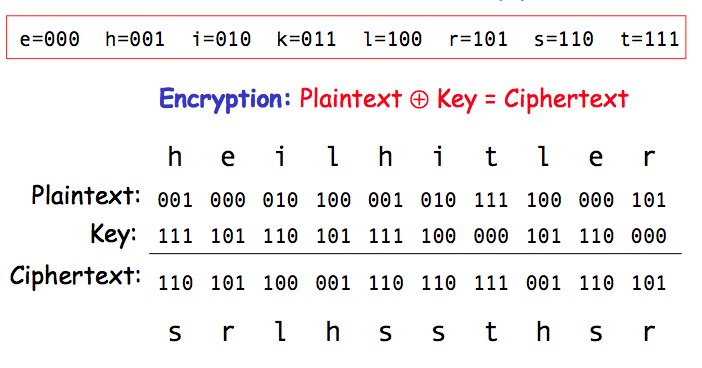
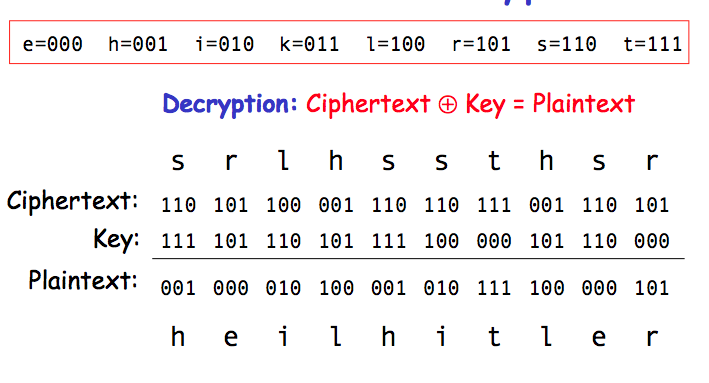
Suppose the ciphertext was intercepted by the Americans and the receiver (thought to be on the American side) was a double agent. A double agent might claim the one-time pad was as follows, and so the receiver should be let go!
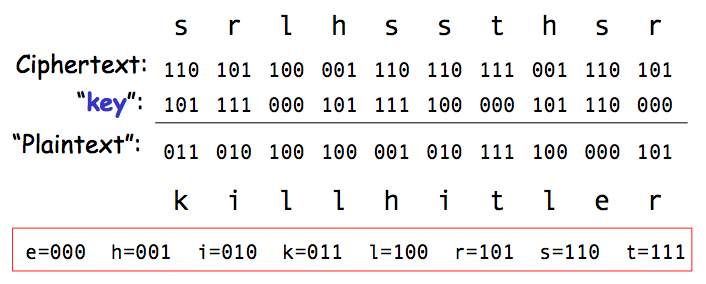
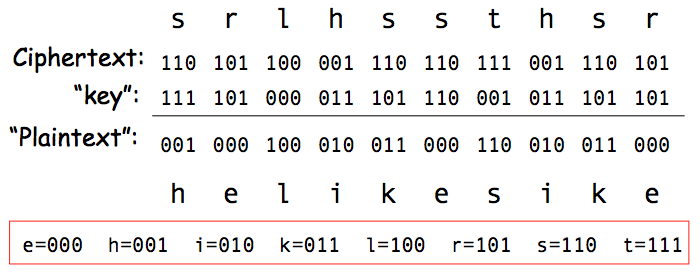
Suppose the ciphertext was intercepted by the Americans and the sender was captured but not the key. The sender might claim the one-time pad was as follows, and so the sender should be let go!
[C% Ruth] learned that her husband [v] was called up by the army but he was not sent to the front. He is a mechanical engineer and is now working at the ENORMOUS [ENORMOZ] [vi] plant in SANTA FE, New Mexico. [45 groups unrecoverable] detain VOLOK [vii] who is working in a plant on ENORMOUS. He is a FELLOWCOUNTRYMAN [ZEMLYaK] [viii]. Yesterday he learned that they had dismissed him from his work. His active work in progressive organizations in the past was cause of his dismissal. In the FELLOWCOUNTRYMAN line LIBERAL is in touch with CHESTER [ix]. They meet once a month for the payment of dues. CHESTER is interested in whether we are satisfied with the collaboration and whether there are not any misunderstandings. He does not inquire about specific items of work [KONKRETNAYa RABOTA]. In as much as CHESTER knows about the role of LIBERAL's group we beg consent to ask C. through LIBERAL about leads from among people who are working on ENOURMOUS and in other technical fields.
(a) Give an example of biometric-based authentication.
A computer which allows you to log in by using your thumb print in a thumb print scanner would be an example of biometric authentication.
(b) Give an example of authentication based on something you have.
You might be allowed in to a building based on whether or not you have a RFID badge with the correct code in it.
(c) Give an example from everyday life where two-factor authentication is used. Which of "something you know", "something you have", "something you are" are used?
To get into my safety deposit box, I go through a door in which my hand is scanned. I then need a key to open the box. This two-factor authentication involves "something you have" (a deposit box key) and "something you are" (a unique hand print).
Februar 13605 fest 13732 finanzielle 13850 folgender 13918 Frieden 17142 Friedenschluss 17149 ...
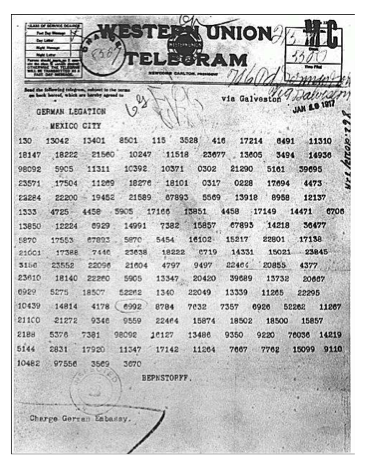


ciphertext plaintext ========== ========= Copenhagen Greenbacks Greece Hayes Rochester votes Russia Tilden Warsaw telegram . . .
From perspective of info available to Trudy