Kerberos, Software Flaws and Malware
CS166
Chris Pollett
Nov 26, 2012











CS166
Chris Pollett
Nov 26, 2012
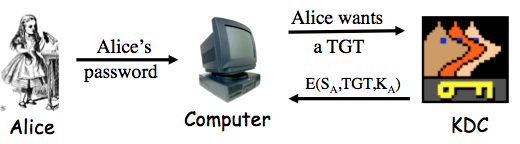
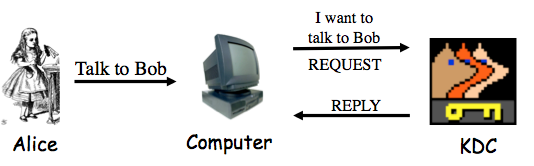
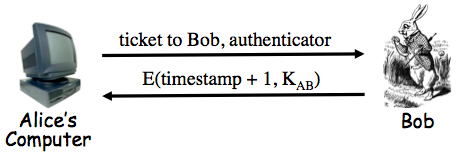
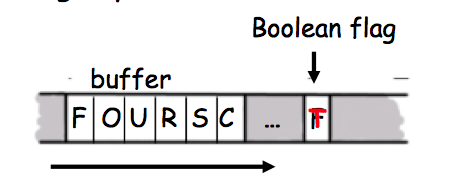
Which of the following is true?
char array[10];
for(i = 0; i < 10; ++i )
array[i] = 'A';
array[10] = 'B';
int main()
{
int buffer[10];
buffer[20] = 37;
}