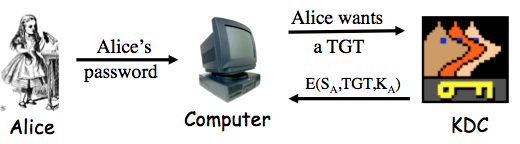
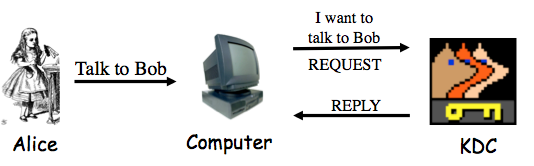
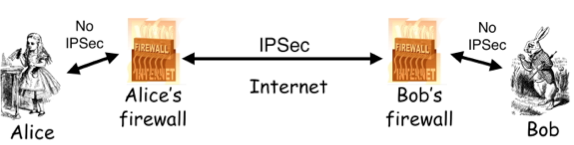
Finish IPSec, Kerberos
CS166
Chris Pollett
Nov 21, 2012











CS166
Chris Pollett
Nov 21, 2012
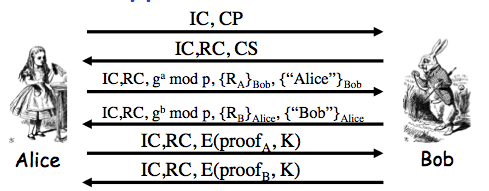
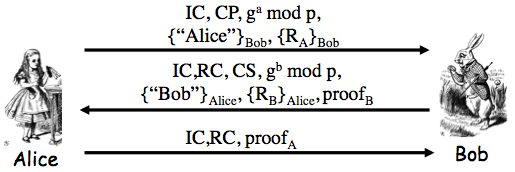
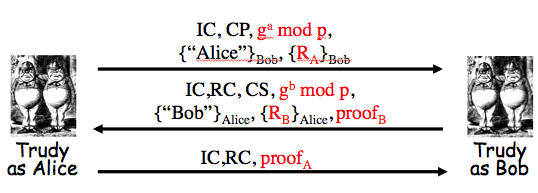
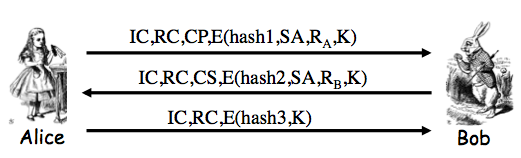
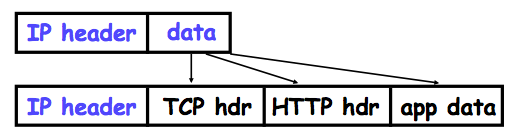
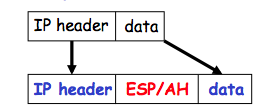
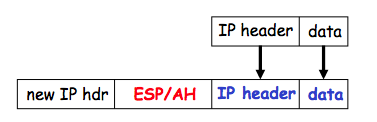
Exercise 10.2. Consider the SSH protocol we gave earlier:
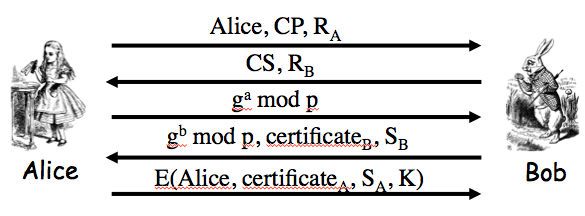
One variant of the protocol allows us to replace Alice's certificate, `c\e\r\t\i\f\i\c\a\t\e_A`, with Alice's password, `p\a\s\s\w\o\r\d_A`. Then we must also remove `S_A` from the final message. This modification yields a version of SSH where Alice is authenticated based on password.
(a) What does Bob need to know so that he can authenticate Alice?
Answer. Alice sends "Alice" and her password encrypted using `K`. So Bob needs to know `g, p`, `g^a mod p` as wells as his `g^b mod p` in order to compute `K = g^(ab) mod p` to decrypt these pieces of information. Then he must look up Alice in his password file and check her password against what he thinks is her password.
(b) Based on Problem 1, part c, Trudy can establish a shared symmetric key `K` with Alice. Assuming this is the case, can Trudy then use `K` to determine Alice's password?
Answer. No. In the next to last message Alice would receive `g^t mod p`, `c\e\r\t\i\f\i\c\a\t\e_B`, `[H_b]_(Bob)` where `h` is:
`H_b = h(Alice,Bob,CP,CS,R_A,R_B,g^t mod p,g^b mod p,g^(bt) mod p)`
However, she is expecting `[H_a]_(Bob)`:
`H_a = h(Alice,Bob,CP,CS,R_A,R_B,g^a mod p,g^t mod p,g^(at) mod p)`
So she would never send the last message.
(c) What are the significant advantages and disadvantages of this version of SSH?
Answer. This version would be faster to compute for Alice (doesn't need to calculate S_A) and she doesn't have to have a certificate. For Bob though it means he must maintain a password file.