Diffie-Hellman, ECC, Uses for Public Key Crypto
CS166
Chris Pollett
Sep. 19, 2012











CS166
Chris Pollett
Sep. 19, 2012
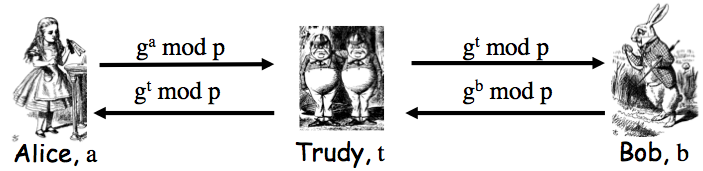
Problem 4.5 In class we showed if we encrypt `M` using RSA with the public key and then decrypt with the private key, we get the original message back. Give the analogous proof that RSA signature verification works. That is, if we encrypt with the private key and decrypt with the public key we get `M` back.
Answer: