More Authentication Protocols
CS166
Chris Pollett
Nov 14, 2012











CS166
Chris Pollett
Nov 14, 2012
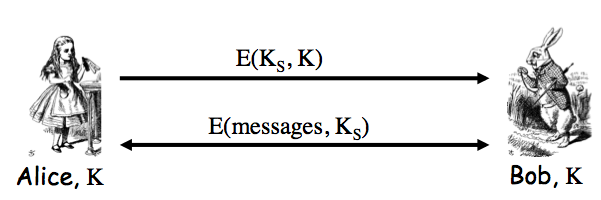
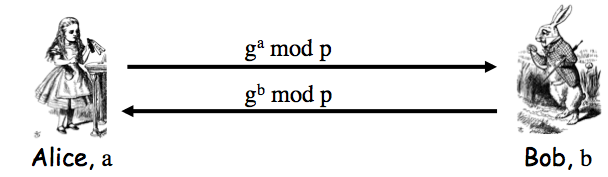
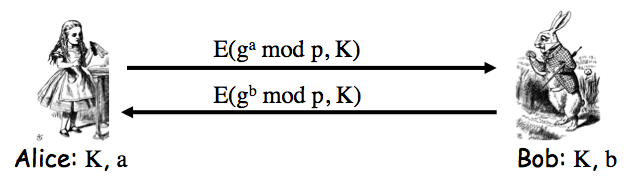

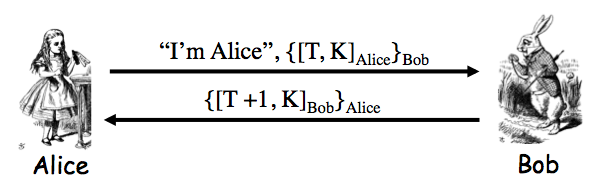
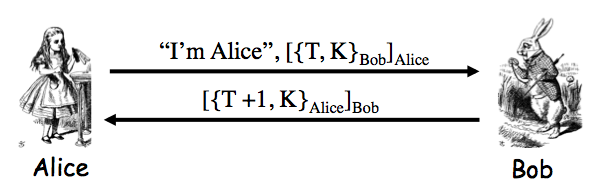
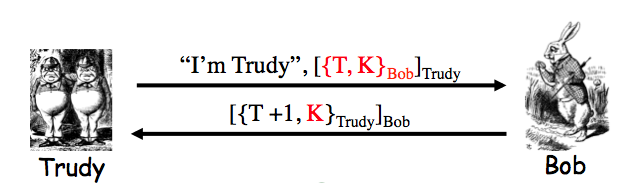
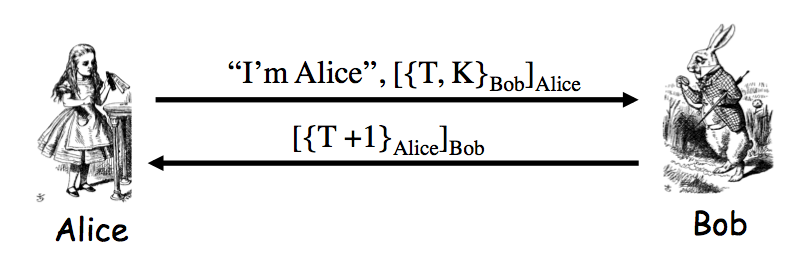
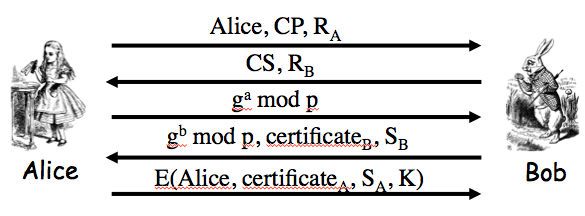
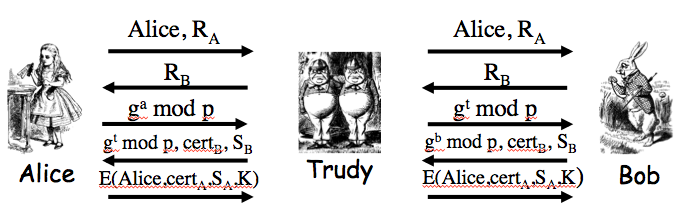
Exercise 9.2. The insecure protocol from two slides back can be modified to the messages Alice-to-Bob: "I'm Alice", `[{T,K}_(Bob)]_(Alice)`; Bob-to-Alice: `[T+1]_(Bob)` to make a secure protocol. Give two other distinct ways to slightly modify the protocol from two slides back so that that the result is secure. Your protocols must use a timestamp and "encrypt and sign".
Answer. The protocol from one slide back is such an answer. Notice there we encrypt using Alice PK `T+1` -- this is slightly better in that we would also not leak the timestamp, although it is likely that Trudy knows the current time already.
Another possibility is Alice-to-Bob: "I'm Alice", `[{T}_(Bob)]_(Alice)`; Bob-to-Alice: `[{T+1,K}_(Alice)]_(Bob)`. Only Bob (besides Alice) can compute `T+1`; only Alice can decrypt to find `K`.
Next, we look at real protocols...