Outline
- Multiple Block Encryption
- ECB
- HW Problem
- CBC
- CTR
- Integrity
Multiple Blocks
- How to encrypt multiple blocks?
- Do we need a new key for each block?
- As bad as (or worse than) a one-time pad!
-
Encrypt each block independently?
- Make encryption depend on previous block?
-
That is, can we �chain� the blocks together?
- How to handle partial blocks?
- We won'�t discuss this issue
Modes of Operation
There are many solutions to this problem -- we discuss three most popular:
- Electronic Codebook (ECB) mode -- Encrypt each block independently.
This is the most obvious solution, but as we will see has some serious weaknesses
- Cipher Block Chaining (CBC) mode -- Chain the blocks together. This is
more secure that ECB, and involves virtually no more computational work.
- Counter Mode (CTR) mode -- Block ciphers acts like a stream cipher. This
is popular for random access.
ECB Mode
-
Notation: `C = E(P,K)`
- Given plaintext written as a sequence of blocks `P_0,P_1,...,P_m,...`
- The most obvious way to use a block cipher is as follows:
| Encrypt | Decrypt |
|---|
| `C_0 = E(P_0, K)` | `P_0 = D(C_0, K)` |
| `C_1 = E(P_1, K)` | `P_1 = D(C_1, K)` |
| `C_2 = E(P_2, K)` | `P_2 = D(C_2, K)` |
| ... | ... |
- For fixed key K, this is �electronic� version of a codebook cipher (without additive).
- Here we imagine a different codebook for each key.
ECB Cut and Paste
- Suppose we have the plaintext:
Alice digs Bob. Trudy digs Tom.
- Assuming 64-bit blocks and 8-bit ASCII:
`P_0` = �Alice di�, `P_1` = �gs Bob. �,
`P_2` = �Trudy di�, `P_3` = �gs Tom. �
- Ciphertext: `C_0, C_1, C_2, C_3`.
- Trudy cuts and pastes this as `C_0, C_3, C_2, C_1`.
- Decrypting this latter yields:
Alice digs Tom. Trudy digs Bob.
ECB Weakness
- Suppose `P_i = P_j`
- So if `C_i = C_j` then Trudy knows `P_i = P_j`
- This gives Trudy some information, even if she does not know `P_i` or `P_j`.
- Trudy might know `P_i` (known plaintext)
- Is this a serious issue?
Alice Hates ECB Mode
Consider the following pair of images of Alice in Wonderland, one the original uncompressed image,
one which is ECB encrypted using TEA:
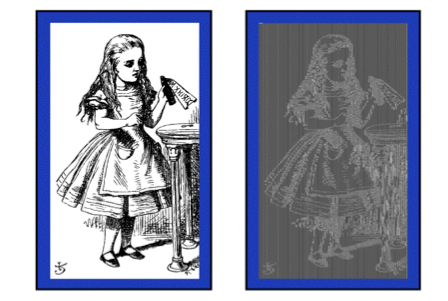
As you can see, encrypted it still looks like Alice -- the blocks of the image contain relatively
few pixels, and a given pattern of pixels will always encrypt in the same way!
Hw Problem
Problem 3.7 The RC4 cipher consists of a lookup table S, which contains 256 byte values, and two indices, i and j.
- The lookup table S is initial identity permutation 0, 1, ..., 255 and at each step of the algorithm S contains a permutation. How is this achieved? That is, why does S always have a permutation?
- Where is RC4 used in the real world?
Solution. (1) There are two places in the algorithm in which the array S is changed. The first is during the initialization phase where
swap(S[i], S[j]); for each 0 ≤ i < 256 and where 0 ≤ j < 256 is determined by a linear function. If the array starts off with each of that values from 0 to 255, a swap preserve the property that for each value between 0 to 255 there is some index with that value. i.e., that we still have a permutation. So after 256 such swaps we still have a permutation. The second place where S is modified is while we are computing the bytestream. Again, the operation is a swap, so the property of being a permutation will be preserved.
(2) According to Wikipedia, RC4 is used in WEP, WPA, and SSL (optionally). It can be used in PDF and is used in a modified form in Skype.
Cipher Block Chaining (CBC) Mode (IBM - 1976)
- In this mode, blocks are chain together.
- A random initialization vector, or IV, is required to initialize CBC mode.
- IV is random, but not secret, and we send it in the clear as the block before `C_0`.
| Encryption | Decryption |
|---|
| `C_0 = E(IV oplus P_0, K),` | `P_0 = IV oplus D(C_0, K),` |
| `C_1 = E(C_0 oplus P_1, K),` | `P_1 = C_0 oplus D(C_1, K),` |
| `C_2 = E(C_1 oplus P_2, K),` | `P_2 = C_1 oplus D(C_2, K),` |
| `...` | `...` |
- This is analogous to a classic codebook cipher with additive.
CBC Mode Remarks
- Identical plaintext blocks yield different ciphertext blocks -- this is good!
- If `C_1` is garbled to, say, `G` then
`P_1 ne C_0 oplus D(G, K), P_2 ne G oplus D(C_2, K)`
- But `P_3 = C_2 oplus D(C_3, K), P_4 = C_3 oplus D(C_4, K),...`
- So we only lose a couple of block, and then can automatically recovers from errors
- Cut and paste is still possible, but more complex (and will cause garbles)
Alice Likes CBC Mode
Performing the same experiment we did with ECB mode, but instead using CBC yields much better results...

Because the same block of plaintext is not always encoded in the same way.
Counter Mode (CTR)
- CTR is popular for random access
- Use block cipher like a stream cipher (again, IV is sent as initial block):
| Encryption | Decryption |
|---|
| `C_0 = P_0 oplus E(IV, K),` | `P_0 = C_0 oplus E(IV, K),` |
| `C_1 = P_1 oplus E(IV+1, K),` | `P_1 = C_1 oplus E(IV+1, K),` |
| `C_2 = P_2 oplus E(IV+2, K),` | `P_2 = C_2 oplus E(IV+2, K),` |
| `...` | `...` |
- CBC can also be used for random access..
- With a significant limitation.
Data Integrity
- Integrity -- we want that we can detect unauthorized writing (i.e., modification of data)
- For example, we might want that inter-bank fund transfers are for the quantity actually wanted.
- Confidentiality may be nice, integrity is critical
- Encryption provides confidentiality (prevents unauthorized disclosure)
- Encryption alone does not provide integrity
- One-time pad, ECB cut-and-paste, etc.
Message Authentication Code (MAC)
- Message Authentication Code (MAC) are often used for data integrity
- As we just said, integrity is not the same as confidentiality -- we are trying
to convince someone that the message was what it claimed to be
- A MAC is computed as CBC residue
- That is, we will roughly do CBC encryption, but save only final ciphertext block as the MAC
MAC Computation
Let's assume the message was `N` blocks long. To compute its MAC, we compute:
`C_0 = E(IV oplus P_0, K),`
`C_1 = E(C_0 oplus P_1, K),`
`C_2 = E(C_1 oplus P_2, K),`
`...`
`C_(N-1) = E(C_(N-2) oplus P_(N-1), K) = MAC`
- The MAC is then sent with IV and plaintext
- The receiver does same computation and verifies that the result agrees with MAC
- Note: the receiver must know the key K
Does a MAC work?
Suppose Alice has four blocks of plaintext:
- Alice computes
`C_0 = E(IV oplus P_0,K), C_1 = E(C_0 oplus P_1,K),`
`C_2 = E(C_1 oplus P_2,K), C_3 = E(C_2 oplus P_3,K) = MAC`
- Alice sends `IV, P_0, P_1, P_2, P_3,` and `MAC` to Bob
- Suppose Trudy changes `P_1` to `X`
`C_0 = E(IV oplus P_0,K), C_1' = E(C_0 oplus X,K),`
`C_2' = E(C_1' oplus P_2,K), C_3' = E(C_2' oplus P_3,K) = MAC' ne MAC`
- That is, error propagates into `MAC'`
- Trudy can�'t make `MAC' = MAC` without `K`
Confidentiality and Integrity
- Encrypt with one key, MAC with another key
- Why not use the same key?
- Send last encrypted block (MAC) twice?
- This cannot add any security!
- Using different keys to encrypt and compute MAC works, even if keys are related
- But, twice as much work as encryption alone
- Can do a little better -- about 1.5 �encryptions�
- Confidentiality and integrity with same work as one encryption is a research topic
Uses for Symmetric Crypto
We wrap-up talking about symmetric crypto by giving some of its uses:
- Confidentiality
- Transmitting data over insecure channel
- Secure storage on insecure media
- Integrity (MAC)
- Authentication protocols (later...)
- Anything you can do with a hash function (upcoming chapter...)























