Outline
- Online Bids
- Spam Reduction
- Quiz
- Secret Sharing
- Visual Cryptography
- Random Numbers
Online Bids
- Last week, we were talking about hash functions and at the end of Wednesday, we briefly went
over some uses of hash functions, today we are going to loook at some of these uses in details... We
begin by considering online bidding.
- Suppose Alice, Bob and Charlie are bidders
- Alice plans to bid `A`, Bob `B` and Charlie `C`
- They don't trust that bids will stay secret; nevertheless, they would like bids
to be made simultaneously without knowledge of other bids.
- One solution possible to this problem:
- Alice, Bob, Charlie submit hashes `h(A)`, `h(B)`, `h(C)`.
- All hashes received and posted online.
- Then bids `A`, `B`, and `C` submitted and revealed
- Hashes don't reveal bids (one way)
- Can't change bid after hash sent (collision)
- But there is a flaw here... If we know that the bids lie in the range $10,000 to $20,000,
we might only have 10,000 things to try to hash to figure out the other bids before `A`, `B`, `C` revealed.
- Might want to share a secret salt first, to solve this problem.
Spam Reduction
- Before accept email, want proof that sender spent effort to create email.
- Here, effort == CPU cycles
- Goal is to limit the amount of email that can be sent
- This approach will not eliminate spam
- Instead, make spam more costly to send
Spam Reduction -- A protocol
- Let
`M` = email message
`R` = value to be determined
`T` = current time
- Sender must find `R` so that:
`h(M,R,T) = (00 ... 0,X)`,
where `N` initial bits of hash value are all zero
- Sender then sends `(M,R,T)`
- Recipient accepts email, provided that...
`h(M,R,T)` begins with `N` zeros and provided `T` is not too long ago.
Spam Reduction -- Protocol Analysis
- Sender: `h(M,R,T)` begins with `N` zeros
- Recipient: Verify that `h(M,R,T)` begins with `N` zeros
- Work for sender: about `2^N` hashes
- Work for recipient: always 1 hash
- Sender's work increases exponentially in `N`
- Small work for recipient regardless of `N`.
- Choose N so that...
- Work acceptable for normal email users
- Work is too high for spammers
Quiz
- The oligarchy PKI trust model is what's used by most browsers.
- The birthday attack can be used to at most half the number of keys you need to search to find a collision.
- RFC 2104 computes an HMAC as `h(M,K)`.
Shamir's Secret Sharing
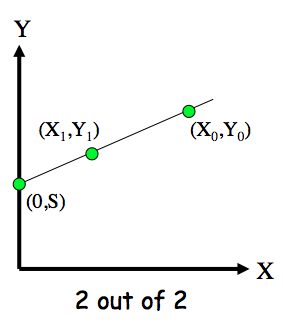
- Two points determine a line
- Give `(X_0,Y_0)` to Alice
- Give `(X_1,Y_1)` to Bob
- Then Alice and Bob must cooperate to find secret `S` (the y-intercept)
- Also works in discrete case
- Easy to make "m out of n" scheme for any `m leq n`
"2 out of 3" Secret Sharing
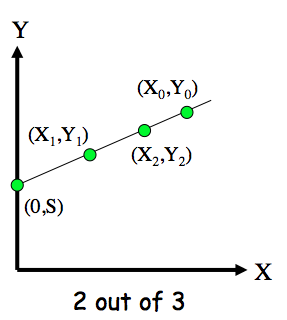
- Give `(X_0,Y_0)` to Alice
- Give `(X_1,Y_1)` to Bob
- Give (`X_2,Y_2)` to Charlie
- Then any two can cooperate to find secret `S`
- But one can't find secret `S`
- A "2 out of 3" scheme
"3 out of 3" Secret Sharing
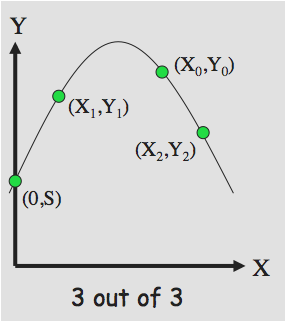
- Give `(X_0, Y_0)` to Alice
- Give `(X_1, Y_1)` to Bob
- Give `(X_2, Y_2)` to Charlie
- Alice, Bob, and Charlie must cooperate to find `S`
- A "3 out of 3" scheme
- What about "3 out of 4"?
Secret Sharing Example
- Key escrow -- suppose it's required that your key be stored somewhere
- Key can be "recovered" with court order
- But you don't trust FBI to store your keys
- We can use secret sharing
- Say, three different government agencies
- Two must cooperate to recover the key
Secret Sharing Example

- Your symmetric key is `K.
- Send point `(X_0, Y_0)` to FBI.
- Send point `(X_1, Y_1)` to DoJ.
- Send point `(X_2, Y_2)` to DoC
- To recover your key `K`, two of the three agencies must cooperate
- No one agency can get `K`
Visual Cryptography
- Another form of secret sharing...
- Alice and Bob "share" an image
- Both must cooperate to reveal the image
- Nobody can learn anything about image from Alice's share or Bob's share
- That is, both shares are required
- Is that possible?
Visual Cryptography
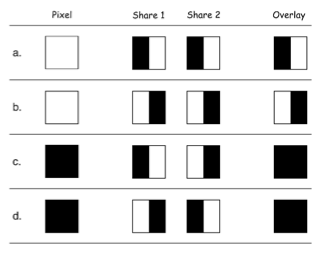
- How to share a pixel?
- Suppose image is black and white
- Then each pixel is either black or white
- We split pixels as shown
Sharing a B&W Image

- If pixel is white, randomly choose `a` or `b` for Alice's/Bob's shares
- If pixel is black, randomly choose `c` or `d`
- No information in one "share"
Visual Crypto Example
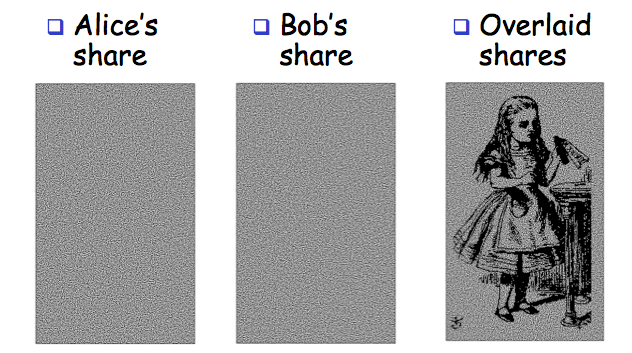
Visual Crypto
- How does visual "crypto" compare to regular crypto?
- In visual crypto, no key...
- With encryption, exhaustive search possible -- Except for a one-time pad
- With visual crypto -- No exhaustive search is possible!
Random Numbers
- Random numbers used to generate keys
- Symmetric keys
- RSA: Prime numbers
- Diffie Hellman: secret values
- Random numbers used for nonces
- Sometimes a sequence is OK
- But sometimes nonces must be random
- Random numbers also used in simulations, statistics, etc.
Such numbers need to be "statistically" random
Texas Hold 'em
- Online version of Texas Hold 'em Poker --
ASF Software, Inc.

- Random numbers used to shuffle the deck
- Program did not produce a random shuffle
- A serious problem or not?
Card Shuffle
- There are `52! > 2^(225)` possible shuffles
- The poker program used a "random" 32-bit integer to determine the shuffle
So, only `2^(32)` distinct shuffles could occur
- Code used Pascal pseudo-random number generator (PRNG): Randomize()
- Seed value for PRNG was function of number of milliseconds since midnight
- Less than `2^(27)` milliseconds in a day.
- So, less than `2^(27)` possible shuffles
Card Shuffle Attack
- Seed based on milliseconds since midnight
- PRNG re-seeded with each shuffle
- By synchronizing clock with server, number of shuffles that need to be tested < `2^(18)`
- Could then test all `2^18` in real time --
Test each possible shuffle against "up" cards
- Attacker knows every card after the first of five rounds of betting!
Redux
- Poker program is an extreme example
- But common PRNGs are predictable
- Only a question of how many outputs must be observed before determining the sequence
- Crypto random sequences not predictable
- For example, keystream from RC4 cipher
- But "seed" (or key) selection is still an issue!
- How to generate initial random values?
- Keys (and, in some cases, seed values)
What is Random?
- True "randomness" hard to define
- In nature, the entropy of a system is a measure of its randomness
- Good sources of "randomness" from nature
- Radioactive decay -- radioactive computers are not too popular
- Hardware devices -- many good ones on the market
- Lava lamp -- relies on chaotic behavior
Software Randomness
- Sources of randomness via software
- Software is (hopefully) deterministic
- So must rely on external "random" events
- Mouse movements, keyboard dynamics, network activity, etc., etc.
- Can get quality random bits by such methods
- But quantity of bits is very limited
- Bottom line: "The use of pseudo-random processes to generate secret quantities can result in pseudo-security"



























