More Reverse Engineering, Operating Systems and Security
CS166
Chris Pollett
Dec 5, 2012











CS166
Chris Pollett
Dec 5, 2012
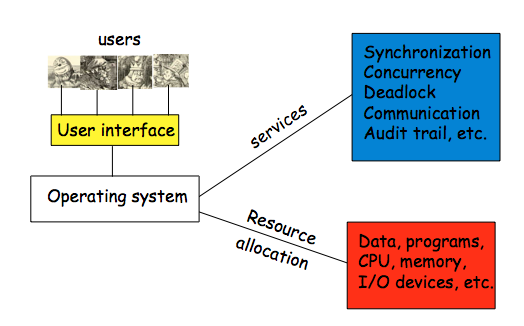
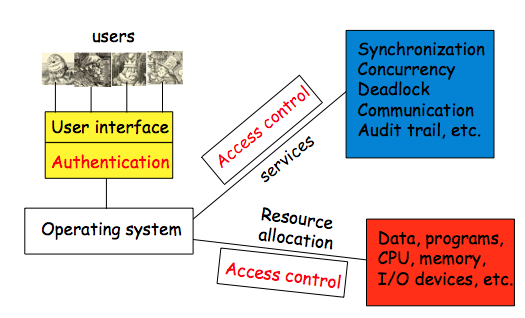
On Monday, we had begun talking about software reverse engineering, and had started talking about some generic tools (dissassembler, debugger, hex editor, etc.) that are useful for this. We now look at some specific examples of these tools
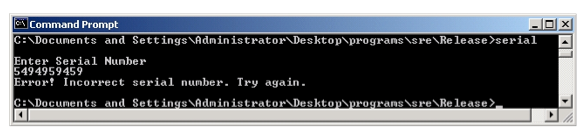
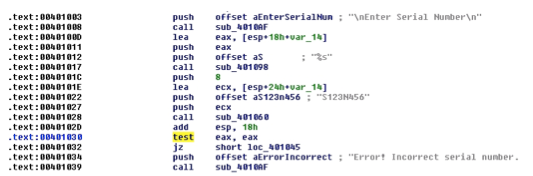
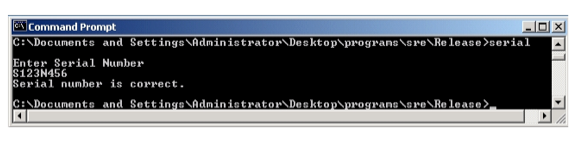



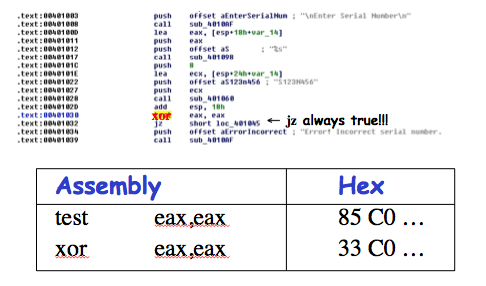
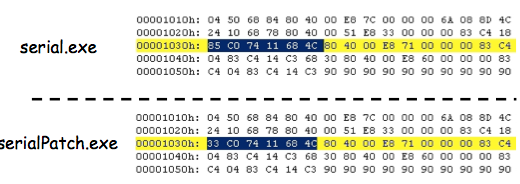
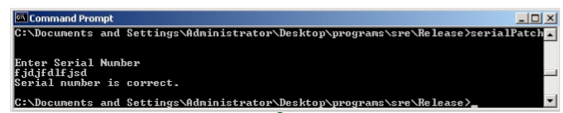

Exercise 13.1 Expand and define each of the following acronyms: TCG, TCB, PITA, MAC, DAC, NGSCB.
Answer.
TCG stands for Trusted Computing Group. It is a consortium led by Intel with the goal of producing a tamper-resistant hardware on which crypto keys etc might be stored.
TCB stands for Trusted Computing Base. This consists of everything in the operating system we rely on to enforce security.
PITA stands for Pain in the A**. It is used when describing how painful it is to deal with some of the secure OS issues.
MAC stands for Mandatory Access Control. It is access that is not controlled by the owner of an object. For example, Alice might have Top Secret clearance but might not be able to completely control access to a document at this clearance.
DAC stands for Discretionary Access Control. It is the access that is controlled by the owner of an object. For example an owner of an object can set its rwx privileges in Unix.
NGSCB stands for Next Generation Secure Computing Base. It is Microsoft's secure operating system features which were originally slated for Vista. It was supposed to have four main feature groups: (a) strong process isolation, (b) sealed storage, (c) secure path to and from mouse, keyboard, etc, and (d) attestation which allowed devices, services, etc to be securely authenticated.
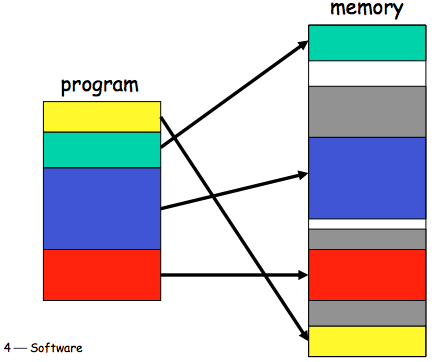
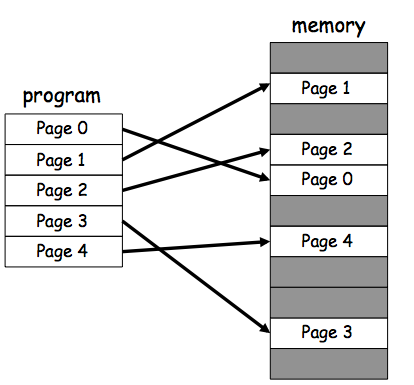
Some people will use slightly different terminolgy for following:
Trust
Security