More B-trees, Hashing and Secondary Storage
CS157b
Chris Pollett
Feb 14, 2018











CS157b
Chris Pollett
Feb 14, 2018
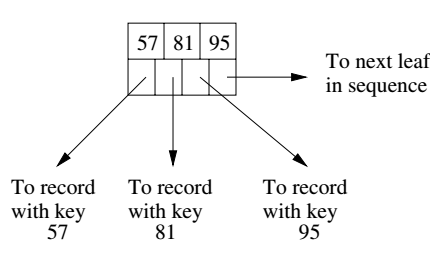
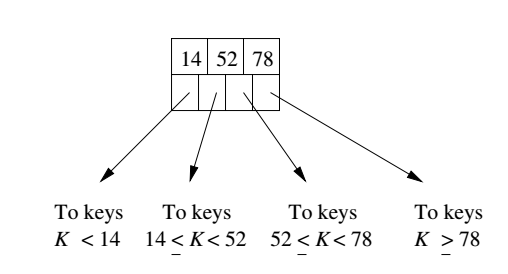
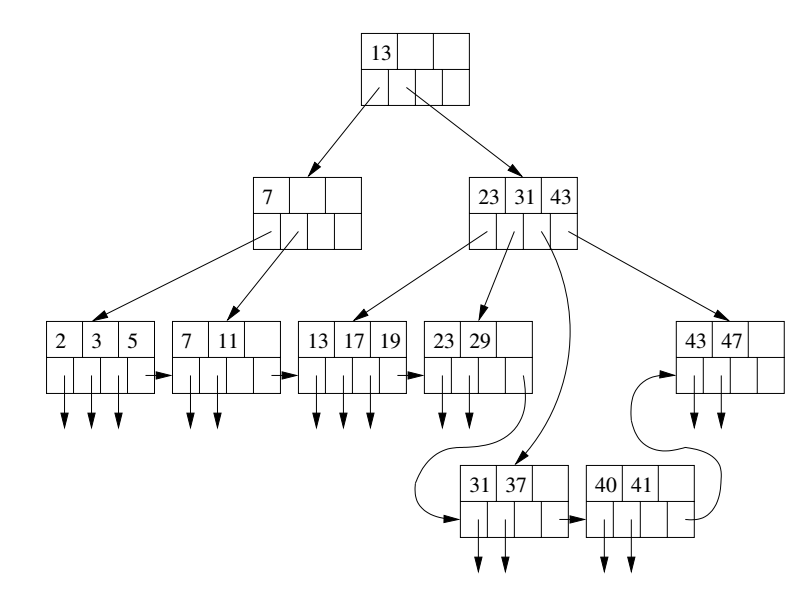
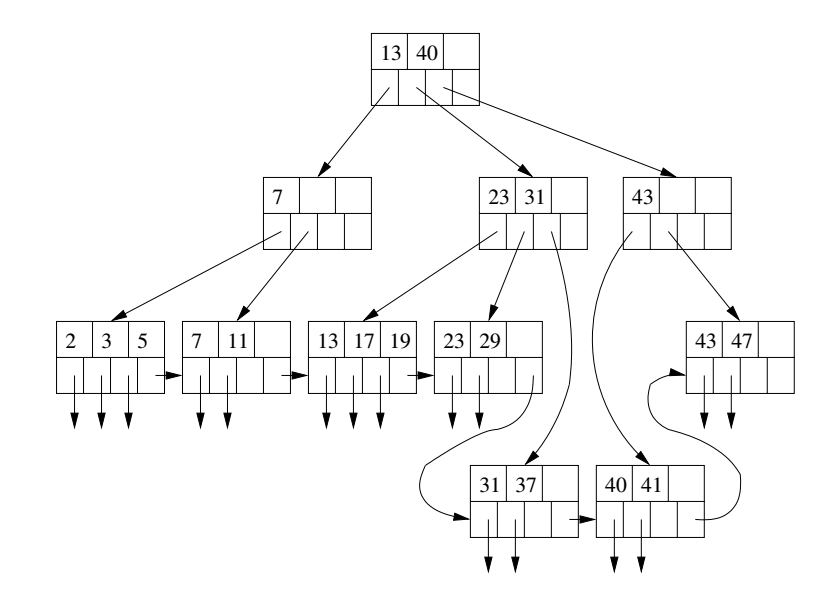
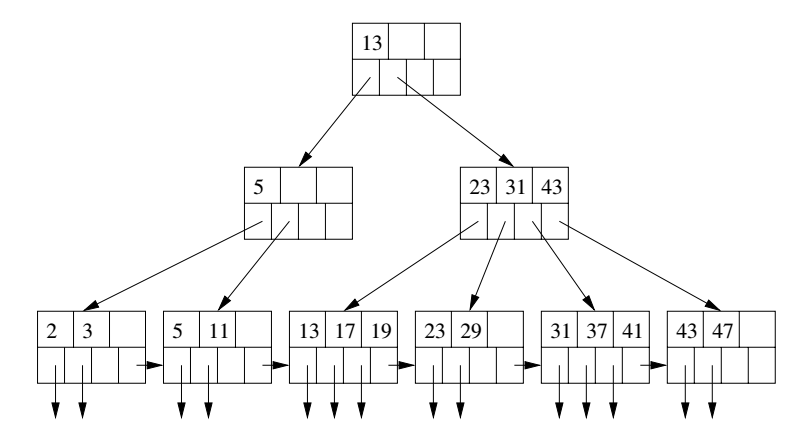
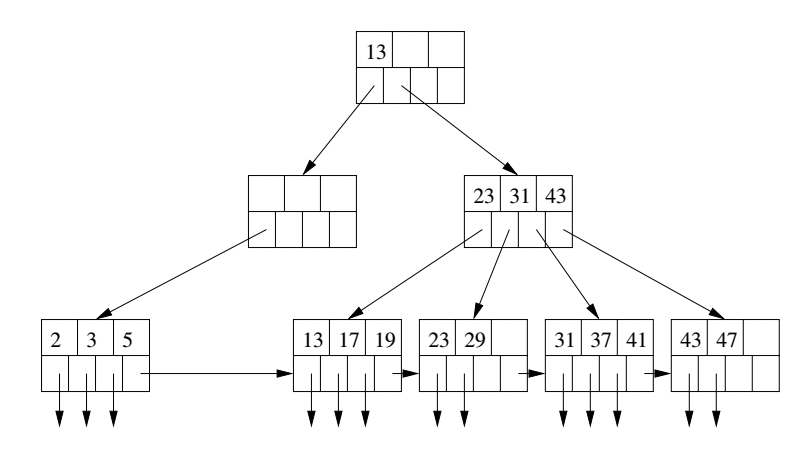
For simplicity we will assume no duplicate keys. To search for a record with key K:
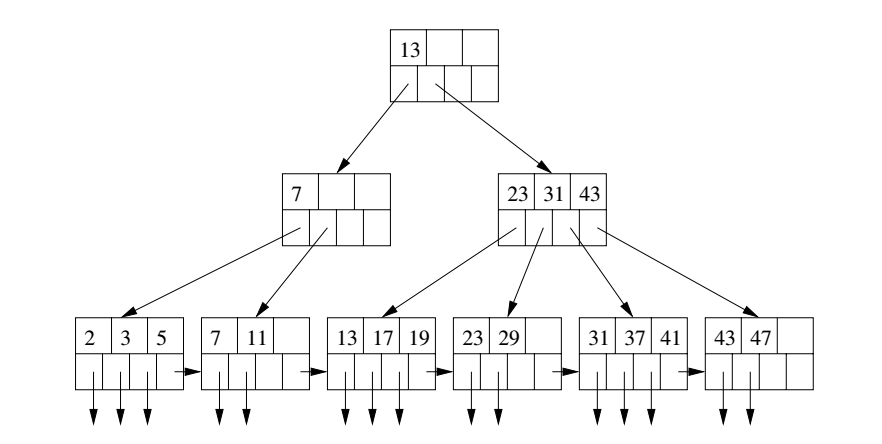
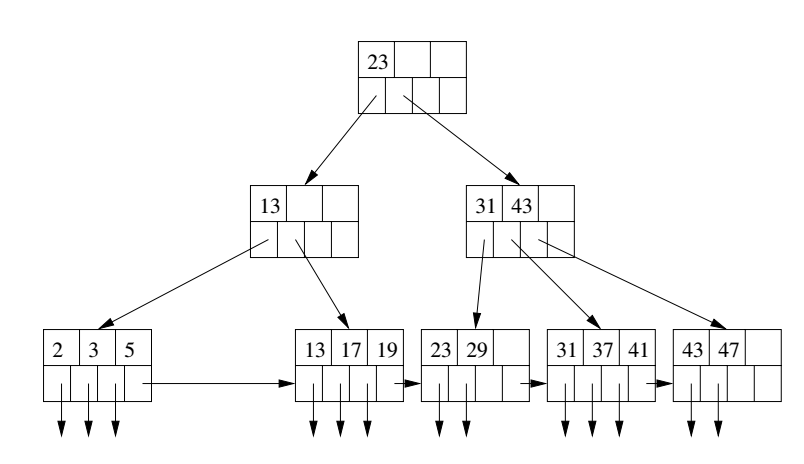
Use the algorithm of the previous slide to step-by-step explain how the record with key 19 would be looked up in the B-tree above.
Post your solution to the Feb 14 In-Class Exercise Thread.
SELECT * FROM R WHERE R.a > 10;